 Firewalld is Fedora’s way to provide dynamic firewall properties in Linux. Thus way changes in the firewall configuration are applied immediately, without the need to restart. Additionally, firewalld supports D-BUS and zone concepts.
Firewalld is Fedora’s way to provide dynamic firewall properties in Linux. Thus way changes in the firewall configuration are applied immediately, without the need to restart. Additionally, firewalld supports D-BUS and zone concepts.
Firewalld replaced Fedora’s old firewall mechanism with Fedora 18. One of the main motivations for a new firewall system was that the old solution required a firewall restart and was thus breaking all statefull connections at each change. Additionally, Firewalld supports dynamic zones which comes in handy when using it with mobile devices as laptops: you can have different zones, thus different sets of rules, for your work network and for your home network.
Besides, to better integrate the system firewall with other applications D-BUS support was integrated into Firewalld, and the configuration is eased for the user via a GUI and a command line helper which is covered here.
If you want to use Firewalld, it might be a good idea to check on which zone you actually are running:
firewall-cmd --get-active-zone home: wlan0
It shows the devices and the given zones.
You can list all available zones by:
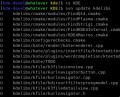
# firewall-cmd --get-zones drop work internal external trusted home dmz public block
So, if you want to change a zone on a network for example because you just started your VPN tunnel to your homenetwork, just do it:
# firewall-cmd --zone=external --change-interface=wlan0
There is no return code shown, unfortunately, but you can query the current zone again to see if it worked.
But since we are talking about dynamic firewall changes, the really interesting part is to open and close ports. Another way to look at it would be to allow or deny the access to services. The difference is that a service can be a list of several ports.
As a result, you can query the enabled services (no ports shown), or enabled ports (no services shown), or list all (everything shown):
# firewall-cmd --zone=home --list-services mdns ipp-client dhcpv6-client ssh samba-client
The story looks different for a zone like external:
# firewall-cmd --zone=public --list-services ssh
The port query looks just the same, but includes the actual port and protocol:
# firewall-cmd --zone=external --list-ports 3333/tcp
As mentioned above, the safest bet is to always query everything:
# firewall-cmd --zone=external --list-all external interfaces: wlan0 services: ssh ports: 3333/tcp forward-ports: icmp-blocks:
As you probably know anyway, if you want to test that the port is actually reachable from the outside, start nc -l 3333 and try to telnet to that port.
But that’s all nothing without the ability, to open and close ports:
# firewall-cmd --zone=external --add-port=2222/tcp # firewall-cmd --zone=external --list-ports 3333/tcp 2222/tcp
Closing the port is just as easy:
# firewall-cmd --zone=external --remove-port=2222/tcp # firewall-cmd --zone=external --list-ports 3333/tcp
As you see the dynamic and zone features of Firewalld work pretty neatly. However, I do not see the benefit of Firewalld for server environments. There you usually have no changing connection trust levels thus no requirement for zones, as far as I see. Also, the dynamics might not be that important, so I wonder if it will play any role at all in the long run on servers.
From a user point of view the dynamic command line helper really comes in handy. It would not hurt to add some more status messages to it, but otherwise it just works. And the zones are partially integrated with NetworkManager, so that in the future different trust levels can be chosen by the user without the need to exactly know what that really means in regard to the actual ports.
Last but not least I am not sure where other distributions stand: will they pick it up? I guess it depends on how tight it will be integrated with tools like NetworkManager or the overall desktop environment…
More information about firewalld can be found in Fedora’s Firewalld documentation.

Gentoo supports Firewalld for both stable and unstable on x86 and amd64